Microsoft Patch Tuesday, December 2025 Security Update Review
As the year winds down, Microsoft Patch Tuesday in December arrives with essential fixes and enhancements to close vulnerabilities and boost performance. Here’s a quick breakdown of what you need to know.
This month’s release addresses 72 vulnerabilities, including three critical and 55 important-severity vulnerabilities.
In this month’s updates, Microsoft has addressed three zero-day vulnerabilities. One of them was exploited, and two were publicly disclosed.
Microsoft has addressed 15 vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, December edition, includes updates for vulnerabilities in Windows Hyper-V, Windows Message Queuing, Windows Defender Firewall Service, Windows Common Log File System Driver, Windows Remote Access Connection Manager, and more.
From elevation of privilege flaws to remote code execution risks, this month’s patches are essential for organizations aiming to maintain a robust security posture.
The December 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 3 | Important: 3 |
| Denial of Service Vulnerability | 3 | Important: 3 |
| Elevation of Privilege Vulnerability | 28 | Important: 38 |
| Information Disclosure Vulnerability | 4 | Important: 5 |
| Remote Code Execution Vulnerability | 19 | Critical: 3 Important: 16 |
Zero-day Vulnerabilities Patched in December Patch Tuesday Edition
CVE-2025-64671: GitHub Copilot for JetBrains Remote Code Execution Vulnerability
A command injection flaw in Copilot may allow an unauthenticated attacker to execute code remotely.
CVE-2025-62221: Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
A use-after-free flaw in Windows Cloud Files Mini Filter Driver may allow the attacker to gain SYSTEM privileges.
CISA acknowledged the vulnerability’s active exploitation by adding it to its Known Exploited Vulnerabilities Catalog and urging users to patch it before December 30, 2025.
CVE-2025-54100: PowerShell Remote Code Execution Vulnerability
A command injection flaw in the Windows PowerShell allows an unauthorized attacker to execute code remotely.
After installing the updates, using the Invoke-WebRequest command triggers a confirmation prompt that warns users about the potential security risks associated with script execution.
Here is the command prompt:
Security Warning: Script Execution Risk Invoke-WebRequest parses the content of the web page. Script code in the web page might be run when the page is parsed. RECOMMENDED ACTION: Use the -UseBasicParsing switch to avoid script code execution. Do you want to continue? ```
For additional details, see KB5074596: PowerShell 5.1: Preventing script execution from web content.
Critical Severity Vulnerabilities Patched in December Patch Tuesday Edition
CVE-2025-62562: Microsoft Outlook Remote Code Execution Vulnerability
A use-after-free vulnerability in Microsoft Office Outlook may allow an unauthenticated attacker to execute code remotely.
CVE-2025-62554: Microsoft Office Remote Code Execution Vulnerability
A type confusion vulnerability in Microsoft Office may allow an unauthenticated attacker to execute code remotely.
CVE-2025-62557: Microsoft Office Remote Code Execution Vulnerability
A use-after-free vulnerability in Microsoft Office may allow an unauthenticated attacker to execute code remotely.
Other Microsoft Vulnerability Highlights
- CVE-2025-62454 is an elevation of privilege vulnerability in the Windows Cloud Files Mini Filter Driver. Successful exploitation of the vulnerability may allow the attacker to gain SYSTEM privileges.
- CVE-2025-62458 is an elevation of privilege vulnerability in the Win32k. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2025-62470 is an elevation of privilege vulnerability in the Windows Common Log File System Driver. Successful exploitation of the vulnerability may allow the attacker to gain SYSTEM privileges.
- CVE-2025-62472 is an elevation of privilege vulnerability in the Windows Remote Access Connection Manager. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2025-59516 is an elevation of privilege vulnerability in the Windows Storage VSP Driver. Successful exploitation of the vulnerability may allow the attacker to gain SYSTEM privileges.
- CVE-2025-59517 is an elevation of privilege vulnerability in the Windows Storage VSP Driver. Successful exploitation of the vulnerability may allow the attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows PowerShell, Windows Projected File System, Windows Storage VSP Driver, Windows Cloud Files Mini Filter Driver, Microsoft Edge for iOS, Windows Resilient File System (ReFS), Windows Win32K – GRFX, Windows Projected File System Filter Driver, Windows DirectX, Windows Client-Side Caching (CSC) Service, Microsoft Brokering File System, Windows Routing and Remote Access Service (RRAS), Azure Monitor Agent, Microsoft Office Access, Microsoft Office Excel, Microsoft Office, Microsoft Office Word, Microsoft Office Outlook, Windows Shell, Windows Camera Frame Server Monitor, Windows Installer, Application Information Services, Microsoft Exchange Server, Microsoft Graphics Component, Copilot, Microsoft Office SharePoint, Storvsp.sys Driver, Windows DWM Core Library,and Microsoft Edge (Chromium-based).
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
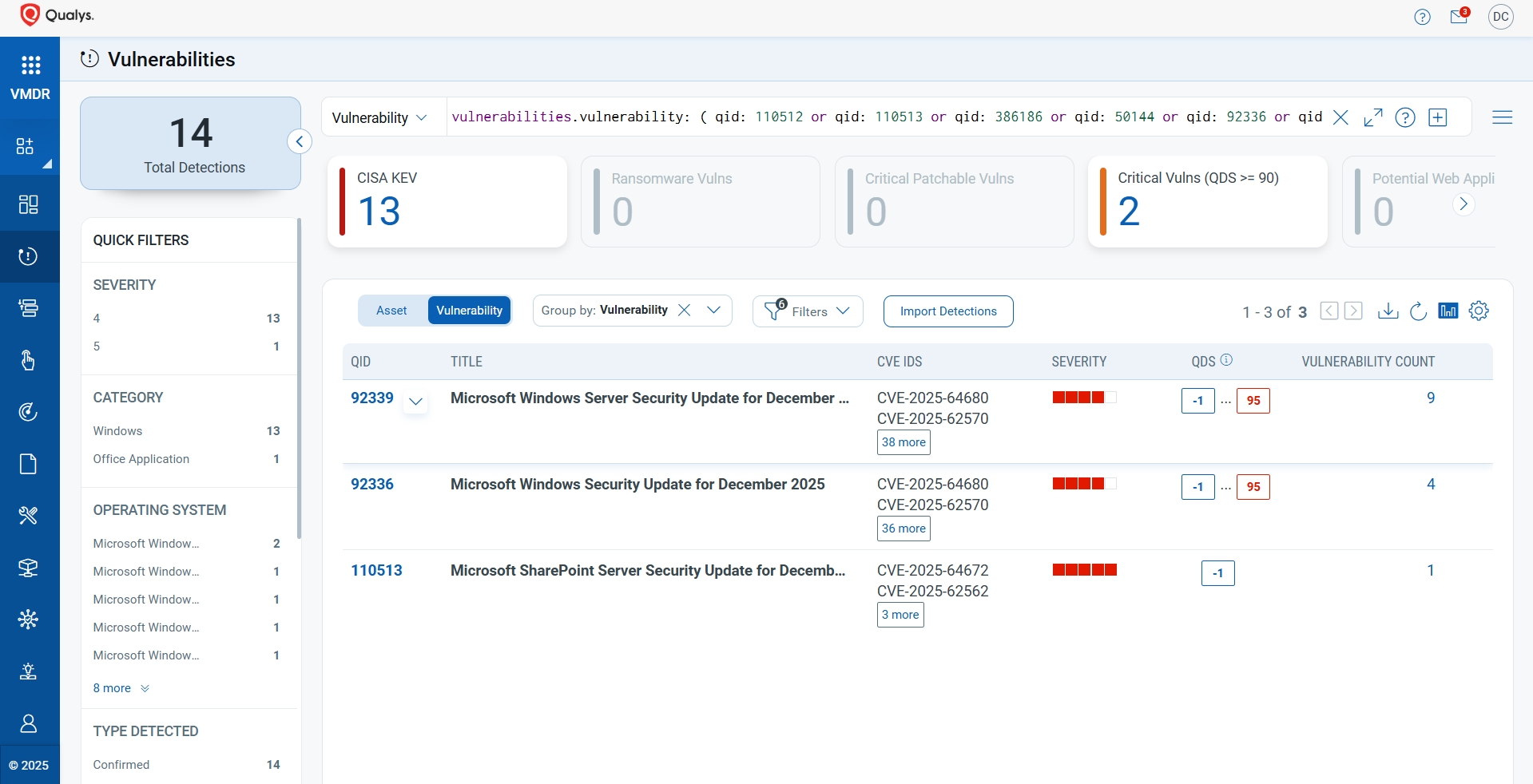
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110512 or qid: 110513 or qid: 386186 or qid: 50144 or qid: 92336 or qid: 92339 )
Rapid Response with TruRisk Eliminate
Eliminate
Patch to the Latest Version
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110512 or qid: 110513 or qid: 386186 or qid: 50144 or qid: 92336 or qid: 92339 )
Visit the December 2025 Security Updates to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110512, 110513, 386186, 50144, 92336, and 92339 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2025-Dec
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-54100
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-64671
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-62221
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-62562
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-62557


Comments are closed.